Anyone who uses the internet will eventually come across:
- attempts to place malware on your computer or device.
- attempts to compromise their identity.
- and attempts to steal account information.
Unfortunately this problem continues to worsen rather than get better simply because the cost to launch these attacks is extremely low. Technical solutions have limited ability to protect you because most threats must exist in the wild before technology can be taught to identify them. The threat window becomes quite wide when users do not consistently keep their computers or devices up-to-date.
This seminar teaches you how to identify these threats as they approach or even as you proceed down the path of compromise. When you can identify a threat you can successfully protect yourself and avoid the time consuming and costly affects of a security compromise.
The seminar is geared towards non-technical users with little knowledge of how the internet works and is offered in two parts;
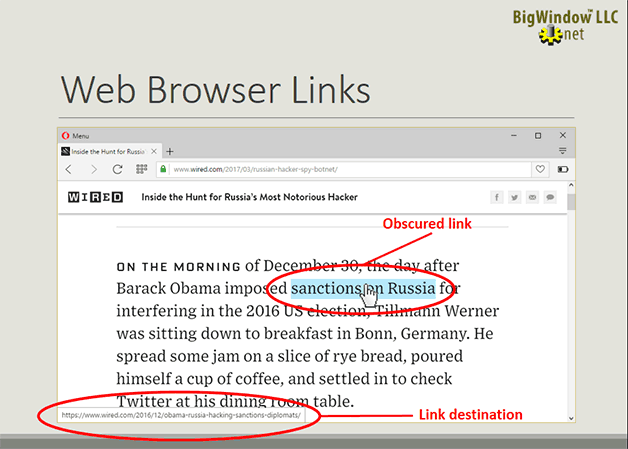
- Internet Addresses: using a comparison between the geographical world you are all familiar with, and the internet world, you walk through how the internet is organized and works. Armed with this information, you learn to identify spaces on the internet that are safe and spaces that are unsafe.
- Understanding Security Breaches: you learn the primary attach surfaces and breach classifications. Using real examples, you’ll work through identifying safe and unsafe territory in email and the web. Part 1 is a prerequisite.
Each part includes 45 minutes of training input and a variable amount of time for question and answer that can be based on your schedule. The parts can be planned back-to-back, offered on different days, or part 1 can be presented individually.
The seminar can be held on-site if you have meeting space with projection capability or a large screen available. Otherwise the seminar is held at the Candy Factory in Lancaster, PA.
Contact us for more information or to schedule this seminar.
